Losing weight, the developer way
August 2015, I decided I need to lose some weight and get healthier. I wasn’t happy with my image and I wasn’t happy that my son kicks my ass in soccer when I get tired after 10 minutes. At that point I was about 105kg – today I am 71kg ![]()
I’ve had a few people ask how I did it, so here is the steps I took and why I went this route rather than a specific diet.
My scrum board
I started off by just tracking what I ate. I had a Windows Phone at the time and found some apps for it. They were pretty quality. What I found useful is to have rough data, use it to compare different food, help understand my choices and that the data should correlate day to day, so you get a feel that today is a good day or a bad day in comparison to history. I moved to Samsung Galaxy S7 which comes with S Health and that is what I use now, it is way better than any Windows Phone option.
Each and every meal was tracked just so I could understand how much is going into me, where the calories, carbs etc.. are coming from and to start to have a way to improve.
Iterative improvement
The next step happened naturally – I started picking what I ate differently because I had more knowledge. My portions also got smaller. This really brought me down to about 90kg just with making smarter eating choices.
I am also not shying away from certain foods, to me there are no bad foods. There are bad amounts and what that amount is is based on the food and varies person to person. You can’t take what works for you and assume it will work for others.
That said though, personally I feel better now that I have lowered the following foods in my diet:
- Wheat
- Dairy
- Sugary drinks
The difference is not to say no, so you end up just thinking of them rather it is taking one piece of toast instead of two cause it makes me feel healthier. This applies to cheat days too, they are kinda smart at helping with willpower management but they just don’t work for me. If I want cake – I eat cake… I just need to work it into the plan for the day.
Remove technical debt
Next was cleaning up my house. No snack foods. No sugary drinks. *sigh*
This was hard but my willpower at 11pm is low. I know my weaknesses so I remove the issues when I am strong so I don’t make mistakes when I am weak.
Cycles
This isn’t just about weight loss, although that is what I have covered so far, it equally is about fitness too. For me, it meant starting to cycle again. This brought up my fitness and helped with about 20kg of weight loss too. It isn’t easy, but it is essential for me. As McDonalds reminds you – it is what you eat and what you do.
Diets don’t work
The problem with diets is that as you lose weight you body needs less calories yet your mind and life don’t change, which leads to fast drops and fast gains. Willpower is hard to do all the time, yet I find when you have data to assist you, it isn’t so much about raw willpower as thinking and I find that is easier. I am approaching this like I would a dev project – learn, implement, review, improve (LIRI).
DevConf - Survival Guide
One role I have often had in companies is assisting teams to get ready for a conference, and with DevConf being next week & my team attending I needed to build a survival guide for them. If you are attending DevConf, then this guide may help you as well!
Configuring Open Live Writer with Drupal 7
 I’ve been using Drupal for 9 years 1 month for this blog and it has served me really well, except working with Windows Live Writer. Every time I reinstalled Windows I had to go through the stupid jumps to get it working again, but thankfully people had documented the process so it was never an issue.
I’ve been using Drupal for 9 years 1 month for this blog and it has served me really well, except working with Windows Live Writer. Every time I reinstalled Windows I had to go through the stupid jumps to get it working again, but thankfully people had documented the process so it was never an issue.
With the introduction of Open Live Writer it changed AGAIN, so this is a guide for you (& me for my next reinstall) on how to configure it.
Drupal
On the Drupal side you need to install the BlogAPI module: https://www.drupal.org/project/blogapi
This provides a bunch of additional features that are needed for it to work.
Make sure the BlogAPI is configured to use the MetaWeblog mode.
Open Live Writer
This is a lot simplier once Drupal is setup
- When adding a blog, select "Other services"
- Set your web address to be similar to this:
http://EXAMPLE.COM/blog/1
< The important part here is /blog/1. Blog should refer to the content type name & 1 should refer to the blog ID. - OLW won't auto detect Drupal, so you need to choose select Movable Type API from the list of options.
- Next, set the remote posting URL to:
http://EXAMPLE.COM/blogapi/xmlrpc
- And move on to finishing the process. A word of note here, it might work getting the theme for the blog yet, this largely depends on your Drupal config & other modules.
Fix the theme loading
I have Taxonomy setup on my blog and it is a required field. The test post that was done to detect the theme would post with a category ‘Uncategorized’, which I did not have.
The second step was once I had setup the blog in Open Live Writer, I had to make a registry change to:
HKEY_CURRENT_USER\SOFTWARE\OpenLiveWriter\Weblogs\<LONG NUMBER>
Inside there is a key called ‘HomepageUrl’ and I had to change that to be where the blog could be found. In my case it pointed to
http://EXAMPLE.COM/users/usernameand changed it to just
http://EXAMPLE.COM.
Join us at DevConf!
Do you miss TechEd? Do you miss a big conference where the passage conversations with the best presenters in the country and from around the world can happen? Do you miss having too many choices for topics to attend cause they all sound great?
I do. The conference space in SA has shifted a lot in the last few years with niche events happening, but very little broad events focused on networking, skilling up and the challenges faced by the modern developer in South Africa who must wear multiple hats. Together with the Developer User Group we are join to fix that!
Come 8th March, in Johannesburg, we will have a new full day conference called DevConf! It has multiple tracks jammed full of content for you including talks convering programming techniques, tools & frameworks, databases, DevOps and the softer skill stuff (like dealing with teams). The event has over 40 speakers including the best from South Africa and internationally. Personally I am so excited to see Willy-Peter Schaub from Microsoft in Canada come out to share about how they use Agile!
Tickets are on sale right now and all the details can be found at http://www.devconf.co.za
The state of testing at Microsoft
Last night I was able to present at the amazing SIGiST (Special Interest Group in Software Testing) meeting run by the IITPSA (Institute of Information Technology Professionals South Africa) and spoke about the changes in Microsoft’s development vision and what tools are available from Microsoft for software testing. It was a great event, and if you are in software testing this is definitely a group you should be attending.
For those unable to attend last night, here are my slides from the talk.
This one weird trick will improve your cell phone signal
Ever notice how you are always on 2G (Edge) mobile networks when you need some data on your phone? A while back I stumbled on this odd trick that seems to always work (at least it does for me & a few other Windows Phone users in South Africa).
Step 1 is go to the settings on the phone – note the E in the status bar at the top, for extremely shitty network.
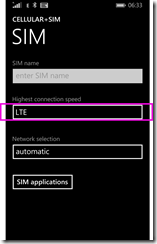
Then on Windows Phone, Cellular + SIM, and click SIM Settings.
Currently it is set to LTE, because SPEED!
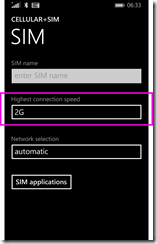
So you then force it to 2G
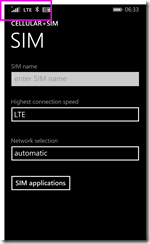
Now, give it a few seconds and change it back to LTE. After about 2 seconds you should lose all network access.
After another few seconds, it will reconnect and it will be on LTE (or sometimes 3G).
Visual Studio Android Emulator + Windows 10 (Build 10547) = Blue Screen
Visual Studio Tools for Cordova + Update 2 + Windows 10 = The mapping file can't be parsed.
If you have VS 2015 and you have installed Update 2, you may run into a painful bug trying to do builds for the Windows 10 store where they just fail with the following errors:
1>MakeAppx : error : The mapping file can't be parsed. The error occurs at line 3. [app\platforms\windows\CordovaApp.Windows10.jsproj] 1>MakeAppx : error : Package creation failed. [app\platforms\windows\CordovaApp.Windows10.jsproj] 1>MakeAppx : error : 0x8007000b - An attempt was made to load a program with an incorrect format. [app\platforms\windows\CordovaApp.Windows10.jsproj] 1>MDAVSCLI : error : Error code 1 for command: C:\Program Files (x86)\MSBuild\14.0\bin\msbuild with args: app\platforms\windows\CordovaApp.Windows10.jsproj,/clp:NoSummary;NoItemAndPropertyList;Verbosity=minimal,/nologo,/p:Configuration=debug,/p:Platform=x86 1> Command finished with error code 2: cmd /s /c "app\platforms\windows\cordova\build.bat --debug --archs=x86 --win --buildConfig=app\build.json" 1>ERROR building one of the platforms : error : cmd: Command failed with exit code 2 1> You may not have the required environment or OS to build this project 1>MDAVSCLI : error : cmd: Command failed with exit code 2
The solution to this is two fold:
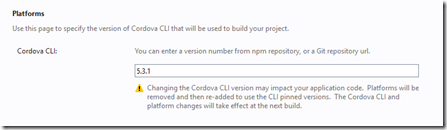
First you need to change the Cordova version to 5.3.1 in the config.xml
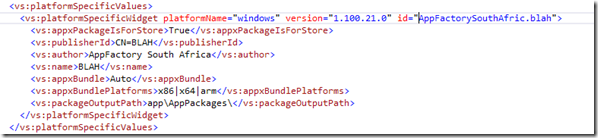
Second you need to open the config.xml in the XML editor (select it in Solution Explorer and press F7) and near the bottom you will find the node vs:platformSpecificValues, delete it and all it contains.
You should now be able to do a Windows 10 build that can be uploaded to the store.
Visual Studio 2015 + Cordova Update 1 can lead to broken Cordova projects
 The dev tools team recently released update 1 for the Visual Studio Tools for Apache Cordova, however this update can cause VS to hang and/or other issues with Cordova projects. This is a known issue and it is one that impacts early adopters most of all because it is the combination of two things that cause this to happen, one being the update the second being the original Windows 10 SDK. There was an issue with the SDK and it was re-released a few days after the initial release with a fix, but anyone with the original bits will have a problem – this includes anyone installing VS 2015 from the ISO while not connected to the internet (if you are connected, even if you use the ISO, it will get the latest bits).
The dev tools team recently released update 1 for the Visual Studio Tools for Apache Cordova, however this update can cause VS to hang and/or other issues with Cordova projects. This is a known issue and it is one that impacts early adopters most of all because it is the combination of two things that cause this to happen, one being the update the second being the original Windows 10 SDK. There was an issue with the SDK and it was re-released a few days after the initial release with a fix, but anyone with the original bits will have a problem – this includes anyone installing VS 2015 from the ISO while not connected to the internet (if you are connected, even if you use the ISO, it will get the latest bits).
Workaround
If you have not yet installed the tools, the check is simple – open the registry and make sure you have the following key:
- For x86: HKLM\Software\Microsoft\VisualStudio\14.0\Setup\VS\JSLS_MSI\Version
- For x64: HKLM\Software\Wow6432Node\Microsoft\VisualStudio\14.0\Setup\VS\JSLS_MSI\Version
if you do not have that registry key, you are at risk of this issue and you should do the following:
Ensure you have an internet connection BEFORE you start this.
- Go to Programs and Features, select Visual Studio 2015, click Change.
- In Visual Studio setup, click Modify.
- Deselect the feature Tools for Universal Windows App Development.
- Select Tools for Universal Windows App Development again, and click Update.
(basically forcing the VS installer to get the latest SDK bits and install those which means the issue doesn’t occur)
If you have already uninstalled the Tools for Universal Windows Apps Development
- Reinstall Tools for Universal Windows App Development.
- Or, take the following steps to reinstall the JavaScript project system and language service:
- Download the installer for your edition of Visual Studio, such as, vs_community.exe.
- Open a command window, and run the following command:
vs_community.exe /modify /installselectableitems JavaScript_Hidden /passive - Change directories to C:\Program Files (x86)\Microsoft Visual Studio 14.0\Common7\IDE
- Run the following commands
devenv /updateconfiguration
devenv /clearcache
(thanks to Paul Chapman on the forums for this information)
Visual Studio ❤ JavaScript
I recently presented at the fantastic JSinSA conference about some of my favourite JavaScript tools that Microsoft is offering. Below are the slides & my demo notes! I also recorded a video the night before of the session so check it out on YouTube.