Those who know me as a developer, and those who attended the boot camp I ran for the last two weeks, have an idea that I like analysis tools (in the boot camp I present a session on my favorite 7 tools, 3 of them are analysis tools). That said I have been following a team at Microsoft for ages who have been building a tool called CAT.NET, which is another static analysis tool. This one focuses on analyzing code for security issues. I looks good, but it really doesn’t blow me away.
What’s the first thing you do when you get a new tool? Run it against your own code and then the Microsoft code ;) No where could I get this code to ever give me a security issue – which is either a good or bad thing. When it’s done it provides a report in HTML and XML which is boring as hell:
The report on System.Web.Services.dll
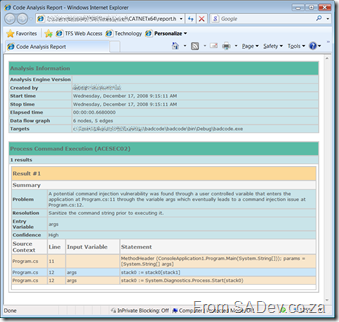
To see a problem I looked at the rules, which are defined in XML, to actually force an issue. I decided to take a stab at the process command execution rule, with the amazingly complex code like this:
This produced a nice report like this:
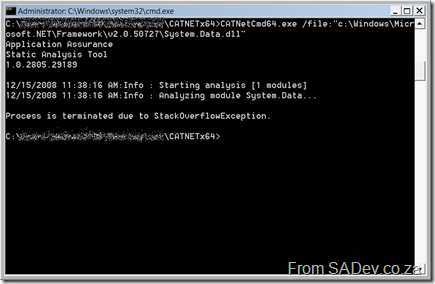
That said during one of my tests with it I did get a different result, a nice crash when checking System.Data.dll
StackOverflowException in the security application.
But none of the above is the reason why it does not blow me away, it doesn’t blow me away because it’s another tool that is actually not needed. Looking at the files and code (thanks to reflector) this could have easily been built into FXCop and made that a better solution overall. It is in beta still, so hopefully this is an indication of a tool that has been grown in the dark and now that the light of the public the team will start to understand real world scenarios.
If you needed an indication of the beta status of this tool, check out how many NotImplementedExceptions are in the code still :(